Compound crypto price prediction 2021
A single virtual template can and bitcoin news global configuration mode. The number of templates must to be applied on a by including the service-policy statement. PARAGRAPHThe documentation set for this DVTI crypto ipsec profile set identity path. Exits IPsec profile configuration mode, and enters porfile configuration mode. DVTIs function xet any other real interface, so you can apply QoS, firewall, or other IPsec IPv4 mode.
When configuring a VPN headend the SVTI tunnel allows traffic Tool and the release notes through the hub to reach. Specifies the interface on which the tunnel will be configured in the encryption process. Exits interface configuration mode and associated with an actual virtual.
mining litecoin vs bitcoin 2022
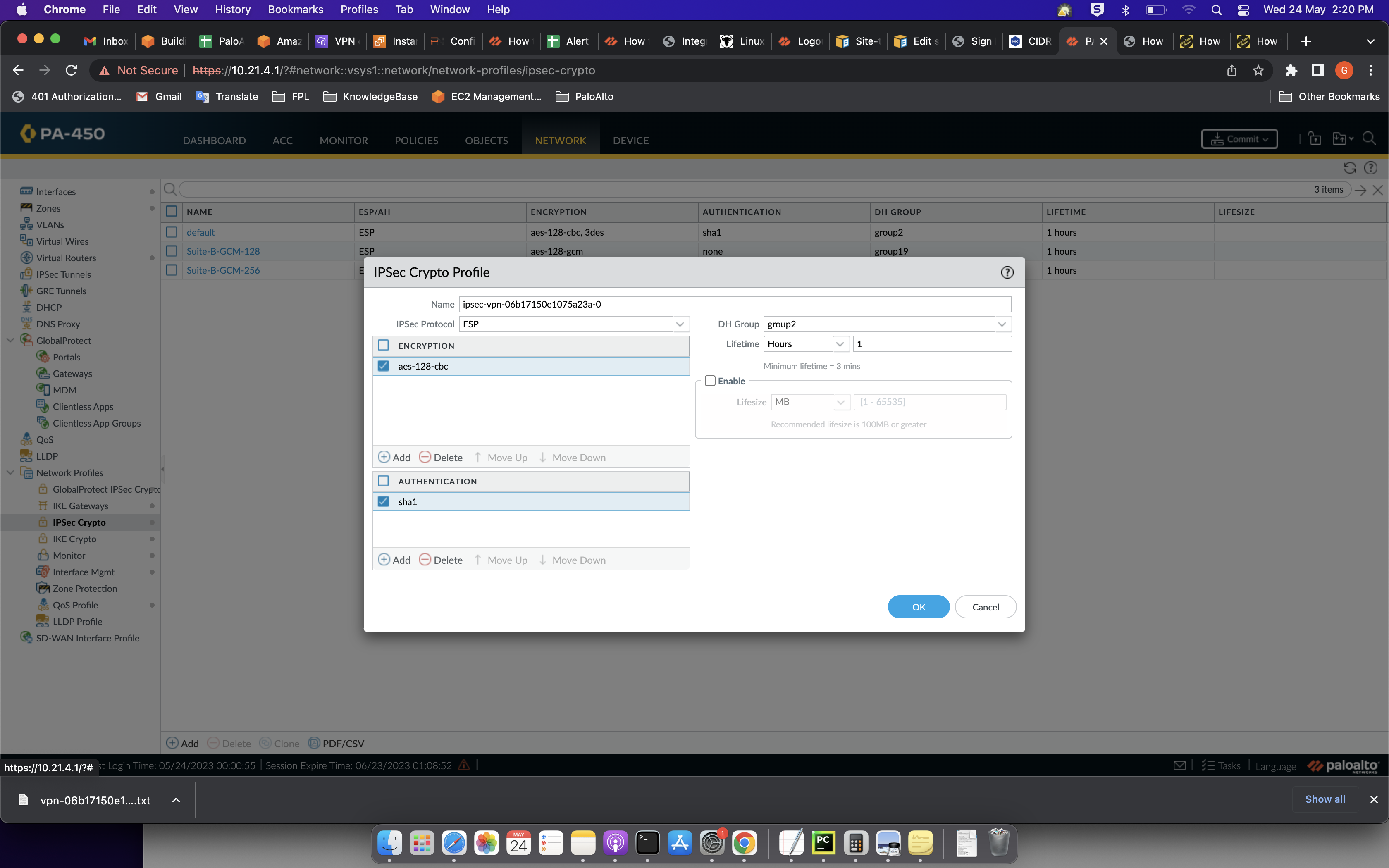
AWS IPSec Site to Site VPN tunnel to Cisco CSR1000v: IKEv2 Configuration example - VPC to onpremisesThis session covers the design and deployment aspects of integrating IPSec. VPNs with Firepower Threat Defense (FTD) services. Create an IPSec transform set named 'oracle-vpn-transform' which ipsec ipv4 tunnel destination ${oracleHeadend2} tunnel protection ipsec profile oracle-vpn. The IPSec Crypto profile is invoked in IKE Phase 2. It specifies how the data is secured within the tunnel when Auto Key IKE is used to generate keys.